1. Outdated Core Software
An advantage of using a website building platform rather than building a site from scratch is that developers will continuously enhance the functionality and security of the platform to provide a seamless user experience.
WordPress developers roll out updates every three months or so. It’s strongly recommended that all WordPress users download these updates when they become available either manually or by enabling auto-updates. Each of these releases typically include improvements, bug fixes, and fixes to more critical security vulnerabilities. So updating your core files can help improve your site’s functionality, performance, and compatibility in addition to security.
Despite the auto-update feature, Santoyo said that, according to Sucuri's database, "50.3% of infected WordPress websites were outdated."
This percentage does look better than the other CMSes like PrestaShop, vBulletin, and Typo3, which had 100% of infected websites running on outdated software. "[But] it's important to note that 50% of WordPress is more websites than the 100% of Typo3 and other platforms. So there's still a significant portion of WordPress websites running on outdated software,"Santoyo said. 
Why are WordPress sites vulnerable?
Outdated core WP software leaves sites vulnerable because updates are usually designed to address critical security issues. Users who don’t download an update are then vulnerable to hackers. For example, WordPress version 5.8.1 included fixes for three major vulnerabilities, including a cross-site scripting (XSS) vulnerability in the Gutenberg block editor.
If your software is outdated, you’re also unable to update your themes and plugins (which we’ll cover below), and your site becomes more vulnerable to many of the security threats on this list.
What You Can Do
WordPress offers automatic updates for each new version of WordPress. You can turn those on in your dashboard to ensure your core files remain up-to-date. If you don’t, then you are leaving your site vulnerable to known threats as well as known threats.

2. Outdated Themes and Plugins
One of the major appeals of WordPress is its customizability. Developers create hundreds of unique themes and plugins that WordPress site owners can use to customize their sites.
However, these extensions require site owners to take proper security precautions. As mentioned above, out-of-date core software can expose your site to security risks, and so can outdated themes and plugins.
In fact, according to data from WPScan, approximately 97% of vulnerabilities in their database are plugins and themes and only 4% are core software.
Sucuri Security saw similar results in its database. “In 2021, vulnerable plugins and extensions accounted for far more compromises than simply having the outdated core on your website," Santoyo said during his WCEU 2022 session.
Why are WordPress Sites vulnerable?
Theme and plugin developers often release updates with functionality enhancements and additional security measures. However, not all developers do.
When they don’t do this, sites using these resources become vulnerable to hackers who can use outdated tools as entry points. For example, say WordPress has released an update with a new security patch but a developer hasn’t updated their theme to be compatible with new requirements. In that case, a hacker could exploit the theme’s vulnerability and gain control of a site.
In addition, if developers do release updates, site owners who fail to install them can make their sites more vulnerable.
What You Can Do
"Whoever is in full management of a website should constantly make sure its inventory of software is up to date," Santoyo stressed during his WCEU session.
Updates serve to improve WordPress themes security and will protect your website. When updates are available for plugins and themes, you can install them manually or use a plugin to automatically install them as they go live.
3. Malware
Malware is a broad term that includes any malicious software (hence, “mal-ware”). Hackers can place malware files in legitimate website files or plant code in existing files to steal from websites and their visitors. The malware could also attempt an unauthorized login via “backdoor” files or wreak general havoc.
In 2021, 61.65% of remediated websites in the Sucuri database were infected with malware. In 2019, 39.53% were, according to Santoyo.

Why are WordPress Sites vulnerable?
Like many of the issues on this list, being vulnerable to malware is directly related to other issues. For example, malware usually enters WordPress sites through unauthorized and outdated themes and plugins.
Hackers take advantage of security problems in plugins and themes, imitate existing ones, or even create entirely new add-ons for the sole purpose of placing harmful code on your site.
For example, AnonymousFox hack was the most popular type of malware infection in 2021. "It is still a major threat to WordPress sites built on cPanel," Santoyo said during his presentation at WCEU. With this hacking tools suite, they get access to your admin panel and install malicious plugins within your file structure, among other genuine plugin files. This is effective because "if not always looking within your file directory, you wouldn’t see it," Santoyo said.
What You Can Do
By default, WordPress restricts the file types users can upload to the media library. If you try to upload a file that isn't included, you'll get an error message, and your file won't upload. Of course, there are ways to get around this as the administrator, but this is one step WordPress takes to stop malware.
Beyond that, here's what you can do: First, carefully vet every plugin and theme you install on your WordPress site. WordPress.com lists valuable stats for all plugins in their directory, like the example below:
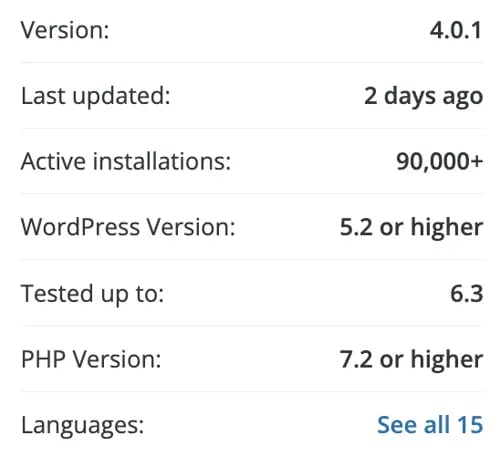
You should also conduct regular security scans to find any potential malware hiding on your WordPress website. "Visibility is the biggest solution," Santoyo said. "That's why monitoring detection can be a good tool: it will tell you exactly what file changes were made in last few days."
Plugins are actually your friend here: there are many strong security plugins out there that can scan for malware and fix damaged files. For example, Defender by WPMU DEV has malware scanning and other features to prevent many of the other issues in this list. You can also explore more options from our list of recommended WP security scanners.
Some hosting platforms offer malware scanning and threat detection built-in, like the free Content Hub. This is a useful alternative if you did not want to rely on WP security scanners.
4. Credit Card Skimming
Credit card skimming is a type of malware designed to steal your customer’s credit card information. Most credit card skimmers inject JavaScript to pilfer payment details entered in payment forms on checkout pages, and are well-hidden in order to avoid detection.
“The single biggest trend is credit card skimming,” Santoyo said during his WordCamp talk. "Last year, one of every three websites running on WordPress had a credit card skimmer detected. From Jan 1 to this Wednesday, two of every three websites had a credit card skimmer detected when pushed through our scanner.” He predicts this is going to become more and more common because WordPress is so popular.
Why are WordPress Sites vulnerable?
By CMS, WordPress takes up the major portion of skimmer infections, with 34.5% in 2021. “Last year, WordPress overtook Magento, a major ecommerce CMS, for having the most credit card skimmers detected,” Santoyo said.

According to data from Builtwith, WooCommerce is the most popular ecommerce platform for the top 1 million sites. “Attackers want the most ROI they can get on attacks like this,” Santoyo said. So it makes sense that credit card skimmer attackers shifted their focus to the most popular ecommerce platform on the web.
Like other security issues on this list, credit card skimmers exploit vulnerable software, weak passwords, and other points of entry. Once they get access to your admin areas, attackers will inject a malicious payload amongst a website’s plugin, theme, or other legitimate files, and obfuscate it in order to harvest as many credit card details from your site as possible.
What You Can Do
“Attackers have more to gain financially from credit card skimmers than other types of infections. So exploit kits are likely going to be more complex and sophisticated because it becomes more profitable for these attackers,” Santoyo explained. As a result, DIY cleanups might become more complex, he said.
His recommended solution is a monitoring tool like Sucuri SiteCheck, which scans your website for known malicious content and malware injections and allows you to see what attackers want your information for.
5. Unauthorized Logins
Unauthorized logins are typically performed by “brute-force.” In a brute-force login, the attacker uses a bot to quickly run through billions of potential username-password combinations. If they’re lucky, they’ll eventually guess the right credentials and gain access to the protected information.
This process looks like the stereotypical cracking-a-code spy scene from movies where a hacker is rushing to gain access to a computer while on the verge of being caught.

Why are WordPress sites vulnerable?
There are two major reasons why these attacks happen successfully on WordPress sites. First, the default backend login page for any given WordPress site is relatively easy to find. Anyone can simply take the site’s main URL, append /wp-admin or /wp-login.php to the end, and they’ll gain access to the login page. If you don’t customize the default login page, attackers can easily gain access and attempt a brute-force entry.
"Always change your wp-admin file and default settings," Santoyo stressed during his WCEU session. "Default settings often invite threats."
In the case of unauthorized WordPress login incidents, the responsibility also falls on the WordPress user. Attackers can easily gain access by pairing the default “admin” username with a simple, common password.
What You Can Do
The easiest and most effective defense against brute-force hacking is a strong password that will be difficult to discover, even with powerful technology that looks like something out of The Matrix. Warnings against weak, predictable passwords are nothing new, but many still aren’t getting the message. (Just read NordPass’s list of the most common passwords of 2019 and weep.)
Allow me to show you why adding just a bit of complexity to your credentials is surprisingly powerful.
The table below shows the approximate time it takes a random brute-force algorithm to guess a password at a rate of around a billion per second, based on password length and use of lower case characters (LC), upper case characters (UC), special characters (SC), and digits.
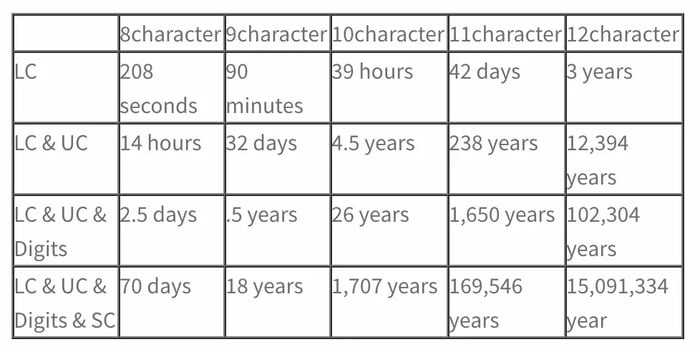
As shown, using a password with a combination of character types and/or length will make it nearly impossible for a brute-force attempt to be successful.
Okay, you’re convinced that strong passwords actually do something. But does thinking of and remembering all these passwords sound like a lot of work? That’s why password managers exist. These handy applications will generate, remember, and safely store your passwords for future use.
In addition to strong passwords, there are additional measures you can take to curb unwanted entries:
- Two-factor authentication requires users to verify their login on a separate device.
- Consider getting rid of the WordPress account with the “admin” username (the first thing hackers will guess) and making a new admin account with a secret username.
- Several reputable WordPress plugins can limit login attempts and add captchas to nip brute-force attacks in the bud. For more details, see our Ultimate WordPress Security Checklist.
Remember that the brute-force method is applicable anywhere there’s a password required, so be sure to fortify your logins for any password-protected information. And don’t repeat them across login pages or leave them face-up on post-its!
Keep in mind that the brute-force method is applicable anywhere there’s a password required, so be sure to fortify your logins for any password-protected information. And don’t repeat them across login pages or leave them face-up on post-its!
6. Undefined User Roles
When you create a WordPress site, there are six different user roles to choose from, like Subscriber or Administrator. Each role comes with native permissions that allow or restrict users from taking specific actions on your site, like modifying plugins and posting content. The default user role is Administrator, and this role has the most control over any given WordPress site.
Why are WordPress Sites vulnerable?
If you have multiple users and don't change the default settings, everyone is an admin, which could become an issue. This doesn’t necessarily mean that the people you’re creating a site with will cause you harm, but it does mean that a hacker who gains access to your site will be able to make changes as an administrator.
Poorly defined admin roles subject your site to increased risk if brute-force attacks are successful, as admin roles can give a hacker complete control over your site. In addition, cross-site scripting (covered below) also gives hackers access to front-end capabilities to obtain additional information from your site visitors.
What You Can Do
Regardless of the purpose of your WordPress site, monitor all permissions. If you’re the sole admin on your site, ensure that you have taken additional security measures to prevent hackers from entering your site, like two-factor authentication or longer passwords. If you assign roles to others, make sure you only give them the necessary permissions. Mistakes can happen, so you also want to make sure that a contributor can't accidentally delete a high-performing post, for example.
7. Structured Query Language (SQL) Injections
SQL is a programming language that is used to quickly access stored data on a specific site. It’s the preferred language on WordPress for database management and, while somewhat secure, malicious parties can use it to take advantage of your site.
During an SQL injection, a hacker gains the ability to view and modify your site’s database directly. Attackers can use the SQL to make new accounts on your site, add unauthorized links and content, and leak, edit, and delete data.
Why are WordPress Sites vulnerable?
WordPress sites are vulnerable to this kind of attack because most are designed to foster a sense of community. Attackers commonly use SQL injections through visitor-facing submission forms, like contact forms, payment info fields, and lead forms. When hackers enter information in these forms, they're not hoping to use your content offer — they’re submitting code that will run and make changes from within.
What You Can Do
The best course of action is to be skeptical of user input. Any form submission on your site is an opportunity for visitors with malicious intent to submit information directly into your SQL database.
Restrict the submission of special characters in visitor submissions. Without symbols, you reduce a string of malicious code into harmless gibberish. Consider using a WordPress form plugin and/or a WordPress security plugin to do this work for you. You can also use a captcha as a final step in the submission process to prevent bots from making injection attempts.
8. Search Engine Optimization (SEO) Spam
These spammy hacks are similar to SQL injections, but they target what any website owner values the most: SEO. These hacks take advantage of your top-ranking pages, fill them with spammy keywords and pop-up ads, and use your hard work to sell items or counterfeit merchandise.
Why are WordPress sites vulnerable?
WordPress sites are vulnerable to these attacks the same way as other security issues on this list: outdated plugins, themes, and core software. Successful brute attacks and undefined user roles can also make your site vulnerable.
These hacks are also harder to detect, which makes them even more dangerous. The hackers will often gain access but wait to make any changes not to raise immediate suspicion. Since they’re SEO-based, these spammy keyword additions are only placed on your high-ranking pages, so you won’t identify them when conducting a site-wide review. The hackers simply insert a keyword here and there within relevant pages, like “cheap Chanel bags,” so your code remains relatively intact.
That means SEO spam is most noticeable to SEO crawlers, as they’ll index your site for the spammy keywords and users searching for Chanel bags (or whatever the spammy keyword is).
What You Can Do
One of the first things you can do is follow the aforementioned security measures like updating on time and defining user roles. You can also use a WordPress security plugin that can run malware scans. We’ve created a list of high-quality security plugins and a security checklist that you can use to protect your site from SEO spam (and other issues on this list).
If you’re keen on identifying these hacks on your own, pay close attention to your analytics data and note any sudden changes in SERP positions or increased site traffic for no apparent reason. You may also be notified by an internet browser that notices your site is featuring in search results for something that doesn’t seem related to your site. If you have coding knowledge, you can sift through your high-ranking pages that seem to be affected and attempt to identify the misplaced keywords.
Regardless of the route you choose to take, it’s essential to target and address these hacks early on because SEO crawlers will strike against your site for spammy tactics, and all the hard work you’ve put in will go to waste.
9. Cross-Site Scripting
Cross-Site Scripting (XSS) happens when an attacker places malicious code into the backend code of the chosen website. XSS attacks are similar to database injections in that attackers try to plant code that runs in your files, but XSS primarily targets web page functionality. Once they get access to your front-end display, hackers might try to harm visitors by, for example, posting a disguised link to a faulty website or displaying a fake contact form to steal user information.
Why are WordPress sites vulnerable?
Again, WordPress plugins and themes are the culprits here. If an attacker finds an outdated or poorly-maintained plugin on your side, they can exploit it for access to files that dictate your website’s front end. The same goes for WordPress themes.
What You Can Do
Update, update, update! Always keep your WordPress Core, plugins, and theme running their latest versions, and be very careful when implementing any third-party software on your website.
Another helpful tool for preventing XSS is a web application firewall (WAF), which inspects traffic and prevents unapproved visitors from entering your system from outside networks. WAFs are easy to set up and maintain, so we recommend browsing reputable WAF plugins to protect your WordPress site from XSS, SQL injections, and other attacks.
10. Denial-of-Service Attacks
A Denial-of-Service (DoS) attack aims to block site administrators and visitors from accessing a website. This is done by sending so much traffic to a targeted server that it crashes, taking down all websites hosted on it. Eventually, the server and its hosted websites are restored, but the reputation of the attacked websites might be difficult to rebuild.
These attacks are often conducted from multiple machines simultaneously (forming a botnet), which hides the original source of the traffic and compounds the volume of spam. This is known as a distributed denial-of-service (DDoS) attack, and it’s a lot worse.
Why are WordPress sites vulnerable?
Like any website, those powered by WordPress need hosting. DoS and DDoS attacks target hosting servers, namely those with limited security in place.
What You Can Do
Don’t just rely on plugins for this one; the best defense against DoS/DDoS attacks is secure WordPress hosting.
You'll need to find a reliable hosting provider that suits your business’ needs and maintains a reputation for taking security seriously. For example, WP Engine’s managed hosting plans include DDos Mitigation tools as well as a high-powered security solution known as Global Edge Security built specifically to secure WordPress sites, this enterprise-grade cyber defense can help prevent DDoS attacks on your site.
11. Phishing
Phishing gets its name from actual fishing, where people cast out line after line hoping to get a bite. When phishing, hackers send out massive amounts of spammy links hoping that at least one person will click on it and have their information compromised. You’ve probably heard about or been exposed to phishing attacks through seemingly legitimate emails in your inbox, or text messages from unknown numbers.
Unfortunately, WordPress is not immune to these spammy practices.
Why are WordPress sites vulnerable?
Like other security issues on this list, WordPress sites become vulnerable to phishing attempts through outdated plugins, themes, software, or lack of security checks for submission and comment forms.
If a user with malicious intent gains access to your site with admin privileges, they can post spammy links for users to click that will compromise their information. Phishing capitalizes off of the trust that users have for you and your content, as it’s unlikely their baseline assumption is that you’re attempting to con them. Hackers can also leave comments on your site pages with links that may seemingly direct a user to additional resources that are spam.
Here’s an example of a spammy comment that entices readers to click a link.

What You Can Do
Protection against phishing involves the usual steps: conduct regular updates, monitor site activity, and use secure passwords. You should also download additional security measures for your site, like ReCAPTCHA, to protect against spammy phishing bots. ReCAPTCHA uses machine learning to understand browsing patterns to distinguish between humans and bots.
12. Supply Chain Attacks
Supply chain attacks also capitalize on one of WordPress’s most beloved features: themes and plugins. There are two ways for this attack to happen: a plugin owner installs malware on customer sites, or a hacker purchases a popular plugin and injects spammy code disguised as an update.
As a result of both methods, hackers are granted access to the backend capabilities of their site. For example, they can access secure files and wreak havoc on site visitors’ secure information or implement additional hacks like SEO spam and phishing.
Why are WordPress sites vulnerable?
WordPress sites are vulnerable to these types of attacks because they’re based on something that you’re supposed to do, and what we recommend doing to combat most of the issues on this list: regular updates.
What You Can Do
Thankfully, supply chain attacks often have a short shelf life because WordPress developers actively identify these fake plugins and themes and quickly ban those affected. However, if one happens to fly under the radar, installing security plugins that run regular checks on your site will quickly identify any vulnerabilities.
It’s also worth backing up your WordPress site data, so you can save it if it becomes compromised. As always, this can be done manually or by downloading additional plugins.
13. Hotlinking
Hotlinking — where others use your work without permission or credit — is one of the worst things to experience as a content creator. Typically, another website will embed content, like images, from your website hosted on your server instead of downloading it themselves. They take advantage of the money you’re spending to keep your site up and running to load the images on their site, which can result in higher monthly bills from your hosting provider.
It’s not a direct spammy attack as the people who are hotlinking likely aren’t hackers, but it is a poor internet practice. If your content is licensed and restricted for your individual use, then hotlinking is not just bad etiquette — it’s illegal.
Why are WordPress sites vulnerable?
As a site owner, you want to share your high-quality content with site visitors. Unfortunately, WordPress sites are vulnerable to hotlinking because people take advantage of this.
They simply copy and paste a link to an image or digital file from another site onto their site without giving credit. Many WordPress site owners might not have the time to take preventative measures against hotlinking — or even think to do so.
What You Can Do
There are a various ways to protect your content from hotlinkers, but an easy option is to add discernible watermarks. It’s a user-friendly solution that won’t necessarily stop all malicious parties, but it will require an additional step to remove your personal tag.
A watermark can simply be your name, website domain, or a copyright trademark logo for registered content. You can personally add this watermark to your content, or you can use the tried-and-true WordPress method: a plugin. Most of the tools on this list are marketed towards photographers but are suitable for anyone hoping to include a watermark on their image (example shown below.)

14. Cross-site Request Forgery (CSRF)
Cross-site request forgery (CSRF) is a vulnerability that allows attackers to influence users to take actions they don’t want to take.
For example, using CSRF, attackers can induce users to change their email addresses, transfer funds, change passwords, or take another action. Depending on the action the user takes, the attacker can gain control of the user account and wreak havoc. If the user is an admin, then the attacker can take complete control of the website.
Why Are WordPress Sites Vulnerable?
WordPress sites using some of the most popular plugins are particularly vulnerable to CSRF attacks. More specifically, plugins that use the function check_url(), like WP Fastest Cache, are vulnerable to CSRF attacks. You can find a detailed explanation in this post on Plugin Vulnerabilities.
What You Can Do
You can prevent CSRF attacks by keeping a close eye on your site’s plugins. Although plugins are essential, don’t blindly trust every plugin you come across.
You can protect yourself from cross-site request forgery by installing a robust WordPress security plugin. There are many great plugins out there, and these can keep you safe from all types of attacks, including CSRF attacks.
You can also prevent this attack by hardening your website via two-factor authentication and disabling file editor and PHP execution in untrusted folders.
Protect What You’ve Created
We all know that the internet can be a scary place. It may seem overwhelming, but it’s important to understand the possible risk and threats that sometimes make the internet scary. It’s especially important if you’ve taken the time to create a personalized, content-rich site on WordPress.
Staying informed about cybersecurity is one of the best ways to defend your online presence, protect your business’s growth, and earn the trust of your customers.
Editor's note: This post was originally published in May 2020 and has been updated for comprehensiveness.
.png?width=112&height=112&name=Image%20Hackathon%20%E2%80%93%20Square%20(33).png)





![Adding a Privacy Policy to Your WordPress Site [Step-by-Step Guide]](https://www.hubspot.com/hubfs/Google%20Drive%20Integration/wordpress%20privacy%20policy_122022-Mar-14-2023-01-13-14-7335-PM.jpeg)




