As businesses continue embracing digital transformation, APIs (application programming interfaces) have become integral to virtually every company’s IT infrastructure. And while APIs are a great way to connect and share data between applications, they also present potential security risks.

That’s why it’s essential to have a comprehensive API security strategy in place. From authentication to secure storage and encryption, security best practices can keep your data safe.
In this post, we’ll explain the fundamentals of API security, including common threats against APIs and the best ways to defend against them so that you can reap the benefits of this technology without the downfalls.
Table of Contents
- What Is API Security?
- Types of API Cyberattacks
- API Security Best Practices
- API Security Testing
- REST API Security vs SOAP API Security
What is API security?
API security is the practice of protecting APIs from cyberattacks and misuse. Proper API security measures ensure that all processed requests to the API are from legitimate sources and valid. Security best practices also ensure that all responses from the API are protected from interception or exploitation.

Free Ebook: How to Use an API
Everything you need to know about the history and use of APIs.
- A History of APIs
- Using APIs
- Understanding API Documentation
- And more!
Download Free
All fields are required.

APIs facilitate the transfer of data, often private, between your system and external users. Therefore, a poorly maintained and insecure API is an unlocked gate to your sensitive data. It's important to use best practices like using VPN over antivirus and real APIs to safeguard your data.
That’s good news for hackers and a huge threat for your customers. If this comes off as alarmist, know that billions of records have been exposed from cyberattacks, many due to insecure APIs.

Malicious actors target big and small companies. API hacks have affected businesses, including Facebook, Venmo, Twitter, and the United States Postal Service. To protect sensitive data, you must integrate API security into your planning and building process.
Why API Security Is Important
While cybersecurity is a broad topic that encompasses all online technologies, APIs present unique challenges.
APIs sit between third-party developers and a company’s resources. These security breaches can harm applications and users, as a hacked endpoint grants direct access to sensitive information.
While the financial impact can be substantial, the damage to your brand may be irreparable. You’ll surely lose customer trust and credibility using your API. Third-party integrated apps may even be harmed by extension.
Types of API Cyberattacks

Before we review the best practices to harden your API, we need to know what we’re up against. Here are the most common attacks against APIs that you should know.
Stolen Authentication
One of the simplest ways to access an API is to hijack the identity of an authorized user. For example, if an authentication token falls into the wrong hands, it can be used to access resources with malicious intent while appearing legitimate.
Cybercriminals will try to guess authentication passwords or break a weak authentication process to gain access.
Man-in-the-Middle Attack
A man-in-the-middle (MITM) attack occurs when a hacker intercepts a request or response between an end user and an API. They may steal the contents of this communication (e.g., login credentials or payment information) or modify the contents of the request/response.
Code Injections
APIs with gaps in authentication and validation are also vulnerable to code injections, in which an attacker sends a script to an application’s server via an API request. This script is intended to expose or delete data, plant false information, and/or harm the application’s internals.
You’ll also see the term “SQL injection” used. This code injection is performed on a SQL database.
Denial-of-Service Attack
Denial-of-service (DoS) attacks overwhelm a server’s resources with API requests to slow, break, or crash the web server. Often, these attacks are made from multiple malicious sources simultaneously — a distributed denial-of-service (DDoS) attack.
API Security Best Practices
Despite these risks, APIs aren’t going away any time soon. Virtually any online application seeking to integrate with others will need APIs.
Every new API presents another opportunity for hackers to exploit personal data. Therefore, anyone overseeing software integration should understand API security measures. These best practices can help protect sensitive data from cyber-attacks and unauthorized access.
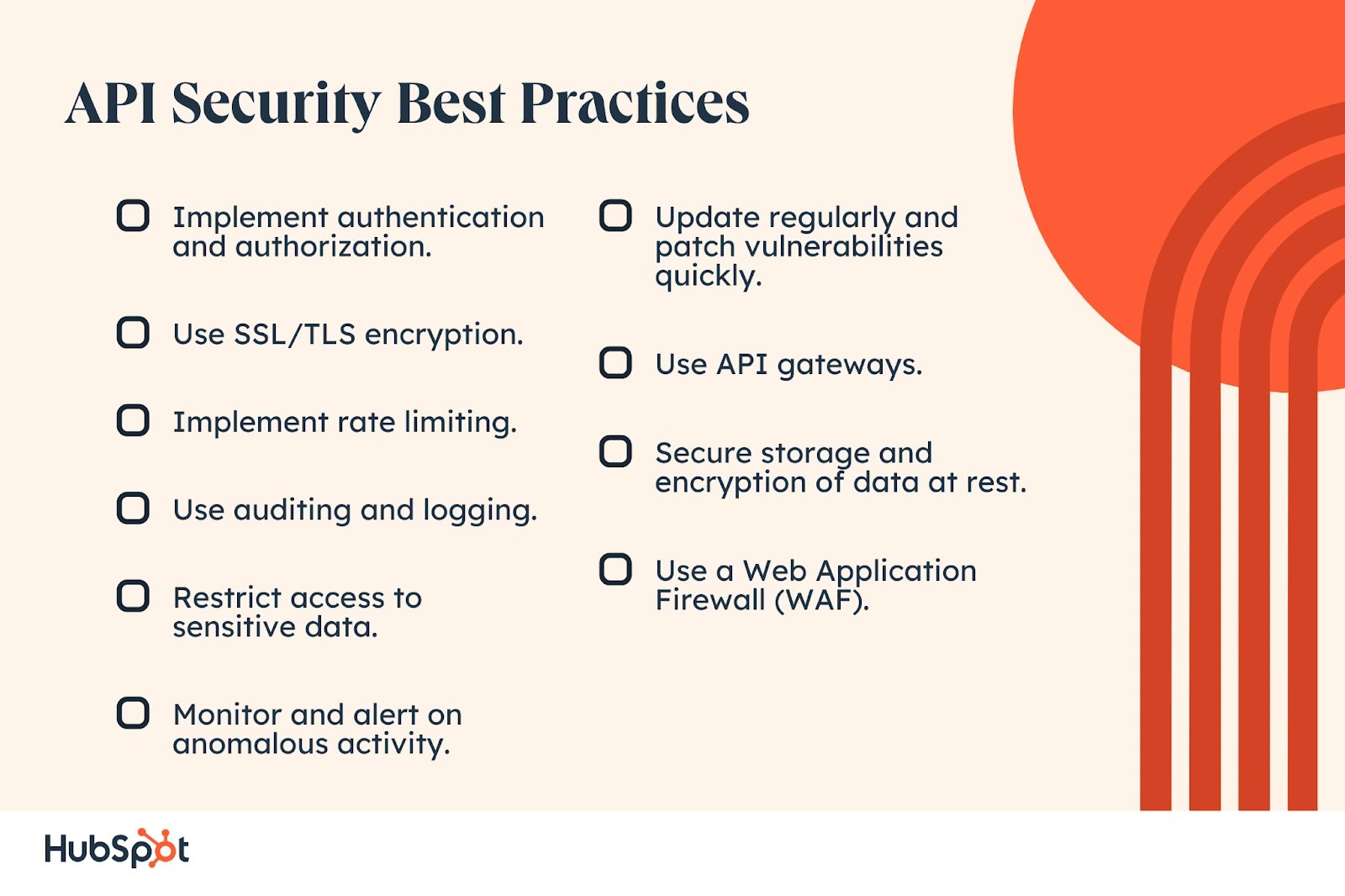
1. Implement authentication and authorization.
The first line of defense against unauthorized access is to implement an authentication system that requires users to provide valid credentials before they can access any data. Authorization is also important, as it dictates what level of access each user has to specific information.
What we like: Authentication and authorization safeguard users from unauthorized access.
Best for: All applications that involve sensitive data or require user authentication.
Pro tip: Enable two-factor authentication (2FA) to provide an extra layer of security to ensure that only authorized people can access the system.
2. Use SSL/TLS encryption.
All communications between APIs and clients should be secured through an SSL connection or TLS encryption protocol like HTTPS. This ensures that all data sent over the wire is encrypted and kept safe from malicious third parties.
What we like: SSL/TLS encryption provides an extra layer of security to protect data in transit.
Best for: Any application that sends sensitive data over the wire or stores private user information.
Pro tip: Ensure your web applications use the latest and most secure version of HTTPS with TLS 1.3 protocol enabled to maximize security.
3. Implement rate limiting.
To protect against malicious automated attacks, you should implement rate limiting on your API calls. This will ensure that requests are promptly processed, and no one user can overwhelm the system with too many requests at once.
What we like: Rate limiting protects against malicious automated attacks.
Best for: Any web application or API that receives multiple requests from the same user quickly.
Pro tip: Set up rate limits tailored to your system's needs and adjust them depending on usage patterns.
4. Use auditing and logging.
It's essential to keep track of what users are accessing and what they’re doing with that information. Make sure to log every API request, and keep audit logs of user activity to ensure data security and compliance.
What we like: Auditing and logging help to keep track of user activity and prevent data breaches or non-compliance issues.
Best for: Any system that stores or transmits confidential information or personal data.
Pro tip: Make sure you have a comprehensive auditing and logging policy in place — and ensure it’s reviewed and updated regularly to keep up with the latest security threats.

Free Ebook: How to Use an API
Everything you need to know about the history and use of APIs.
- A History of APIs
- Using APIs
- Understanding API Documentation
- And more!
Download Free
All fields are required.

5. Restrict access to sensitive data.
If possible, restrict access to sensitive data such as banking information or health records. This can be done through authorization policies or by encrypting the data before it’s transmitted over the network.
What we like: Restricting access to sensitive data is a great way to protect against potential data theft or misuse.
Best for: Any systems that handle important personal or financial information.
Pro tip: Evaluate different methods such as authorization policies, encryption, tokenization, etc., and use the one that works best for your application needs.
6. Monitor and alert on anomalous activity.
Set up a system to monitor user behavior and alert you if suspicious activity is detected, such as multiple failed attempts to access a certain endpoint. This will help you detect and stop malicious activities before they become a bigger issue.
What we like: Setting up a system to monitor user behavior and alert you of suspicious activities can help you detect and stop malicious attacks before they become a bigger issue.
Best for: Any web application that requires authentication or carries sensitive data.
Pro tip: Use automated tools to scan your systems regularly and set up alerts for any unusual activity. Enhance your system security by leveraging popular vulnerability scanners through automated tools.
7. Update regularly and patch vulnerabilities quickly.
Make sure to keep your APIs up-to-date with the latest security patches, as well as any new features or bug fixes that may be released. This can help prevent attackers from exploiting any known vulnerabilities.
What we like: Keeping your APIs up-to-date ensures that all known vulnerabilities are patched, which can help protect against potential attackers.
Best for: Any applications that have regular updates or bug fixes released.
Pro tip: Stay on top of the latest security updates and make sure they’re applied as soon as they become available.
8. Use API gateways.
API gateways can help protect your APIs from malicious attacks by acting as a “gatekeeper” between the client and the API. It will filter out any suspicious requests and block them before they reach their destination.
What we like: API gateways act as “gatekeepers” between the client and the server, protecting against malicious attacks before they reach their destination.
Best for: Any application that receives a large number of requests from outside sources.
Pro tip: Choose an API gateway with advanced filtering capabilities to maximize protection against potential threats.
9. Secure storage and encryption of data at rest.
Any data that’s stored locally should be encrypted to prevent unauthorized access. This includes any backups or snapshots of your data that may be taken.
What we like: Ensuring that all data stored locally is encrypted prevents access from unauthorized individuals or programs.
Best for: Any application where sensitive data is stored in local databases or backups.
Pro tip: Make sure you use multiple layers of encryption when storing confidential information to maximize data security.
10. Use a Web Application Firewall (WAF).
A WAF is a piece of security software that sits between your API and the internet, filtering out any malicious traffic before it reaches your server. It’s a great way to protect against DDoS attacks and other malicious activities.
Best for: Any web application or API facing external traffic, such as those exposed via public websites or mobile apps.
Pro tip: Select a WAF that can be easily customized to your specific needs — allowing you to set different levels of security based on different access points or user roles within the system. Then, make sure your WAF is regularly updated to ensure the latest security patches are applied—keeping your data and applications secure.
Ensure all the above best practices are implemented throughout your entire application stack, not just the API layer. This will ensure comprehensive security for all your data, regardless of where it resides.
API Security Testing
The first step of API security is ensuring your API works as expected. That means submitting regular requests via an API Client and ensuring they stick to the above principles. Develop scenarios that answer the following:
- Can only authenticated users access your endpoints?
- Are users granted access to only the necessary endpoints based on their roles?
- Is the correct information returned in responses for each potential request?
- Are benign but invalid requests rejected?
Once you've established that your API works normally, you’ll need to simulate code injection, MITM, DoS, and stolen password attacks against your systems in a proper testing environment. Address the following in your tests:
- Can my authentication counter brute-force entry attempts?
- How does my API handle significant spikes in requests?
- What if an authenticated user submits a harmful script or file via a request?
- Are all data transfers encrypted? Are requests without TLS/SSL (i.e., with HTTP and not HTTPS) prohibited?
- What if a request or response is intercepted? How will my API and the user know?
Below are some specific tests you can run.
Note: Perhaps you don’t have the in-house staff to perform these tests. Seek out consultants who can provide this area of expertise to help.

User Authentication Test
If authentication mechanisms are implemented incorrectly, attackers can compromise authentication tokens or exploit implementation flaws to assume other users’ identities and gain access to your API’s endpoints.
To test your authentication mechanisms, try sending API requests without proper authentication. See if your API responds with the correct error and messaging. Try this test with both no credentials and incorrect ones.
Parameter Tampering Test
To run a parameter tampering test, try various combinations of invalid query parameters in your API requests and see if it responds with the correct error codes. If not, your API likely has some backend validation errors that must be resolved.
Injection Test
Try injecting SQL, NoSQL, LDAP, OS, or other commands in API inputs. Then, see if your API executes them. These commands should be harmless, like reboot commands or cat commands.

Free Ebook: How to Use an API
Everything you need to know about the history and use of APIs.
- A History of APIs
- Using APIs
- Understanding API Documentation
- And more!
Download Free
All fields are required.

Unhandled HTTP Methods Test
Most APIs have various HTTP methods to retrieve, store, or delete data. Sometimes web servers will give access to unsupported HTTP methods by default, which makes your API vulnerable.
To test for this vulnerability, try all the standard HTTP methods (POST, GET, PUT, PATCH, and DELETE) and a few uncommon ones.
Send an API request with the HEAD verb instead of GET, for example, or a request with an arbitrary method like FOO. You should get an error code. If you get a 200 OK response, your API has a vulnerability.
Fuzz Test
Fuzz testing should be one of the last steps of your API security auditing process. This type of testing pushes your API to its limits to discover any security issues that have yet to be revealed.
To achieve this, send a large number of randomized requests, including SQL queries, system commands, arbitrary numbers, and other non-text characters. Then, see if your API responds with errors, processes any of these inputs incorrectly, or crashes.
This type of testing will mimic Overflow and DDoS attacks.
An API manager or gateway tool will handle or help address the API security guidelines described above (including testing). Let's take a closer look at these tools below.
API Security Management
With an API management platform, you can secure all your APIs and endpoints across environments and vendors in one place. You can also automate parts of the API security process by assigning pre-configured security authentication profiles, creating and customizing policies that can be used to secure all APIs or individual ones, and so on.
Arguably, the most important function of API management platforms is access control. They should prevent unauthorized users from gaining inappropriate levels of access to your API’s services and data.
To enforce access control, most API management platforms support at least one or all three types of security schemes outlined below:
- API key. A single token string that provides unique authentication information.
- Basic authentication. A two-token string solution, like a username and password, that provides unique authentication information.
- OpenID Connect (OIDC): A simple identity layer on top of the OAuth framework, which verifies users by obtaining basic profile information, for example, and using an authentication server.
To discover some popular API management platforms that can help you secure your APIs, check out What Is an API Gateway & How Does It Work? [+Best Service Providers].
The focus of this post has been on REST APIs since they account for approximately 83% of APIs today, but any API is at risk for security breaches. That's why we'll go over the key differences between REST API security and the security of another common API type: SOAP.
REST API Security vs. SOAP API Security
Software developers may follow different architectures to build an API. The most popular are Representational State Transfer (REST) and Simple Object Access Protocol (SOAP).
REST APIs transfer data via the Hypertext Transfer Protocol (HTTP). Meanwhile, SOAP encodes data in XML — a common markup language for storing and transferring information — and sends it via HTTP.
SOAP is more strict in its requirements than RESTful design, making this API type more challenging to build. However, it also tends to be more secure and better at preserving data integrity than other API designs.
Let’s break down their differences below.
RESTful API Security
The RESTful protocol supports SSL to protect data when transferred but lacks built-in security capabilities, including error handling. It also does not support the Web Services (WS) specifications, so you can’t use security extensions like Web Services Security for enterprise-grade security.
That means the security of REST APIs depends on the design of the API itself or an API gateway.

SOAP API security
Like RESTful, the SOAP protocol also supports SSL to protect data when transferred, but it goes further.
Not only does it include SAML tokens, XML encryption, and XML signatures (based on W3C and OASIS recommendations), which help secure the data being sent and received by SOAP APIs — it also supports the Web Services (WS) specifications.
This lets you use security extensions like Web Services Security for enterprise-grade security and WS-ReliableMessaging, which provides built-in error handling.

Protect Your Users By Protecting Your API
API technology brings a myriad of possibilities to online applications, but a security incident can quickly eclipse any benefits you get from an API. While it’s impossible to eradicate all threats, the principles above are necessary for any organization that cares about its reputation and, more importantly, its customers.
Editor's note: This post was originally published in December 2020 and has been updated for comprehensiveness.
![Download Now: How to Use an API [Free Ebook]](https://no-cache.hubspot.com/cta/default/53/1cbd6f4c-4566-446c-852a-0a9dae73e987.png)





![What is Payload? A Quick Guide [+ Examples]](https://www.hubspot.com/hubfs/payload.webp)

